Data sovereignty with clear ownership and jurisdiction
Zero exposure to the CLOUD act, the patriot act and FISA 702.
Data sovereignty with clear ownership and jurisdiction
Zero exposure to the CLOUD act, the patriot act and FISA702
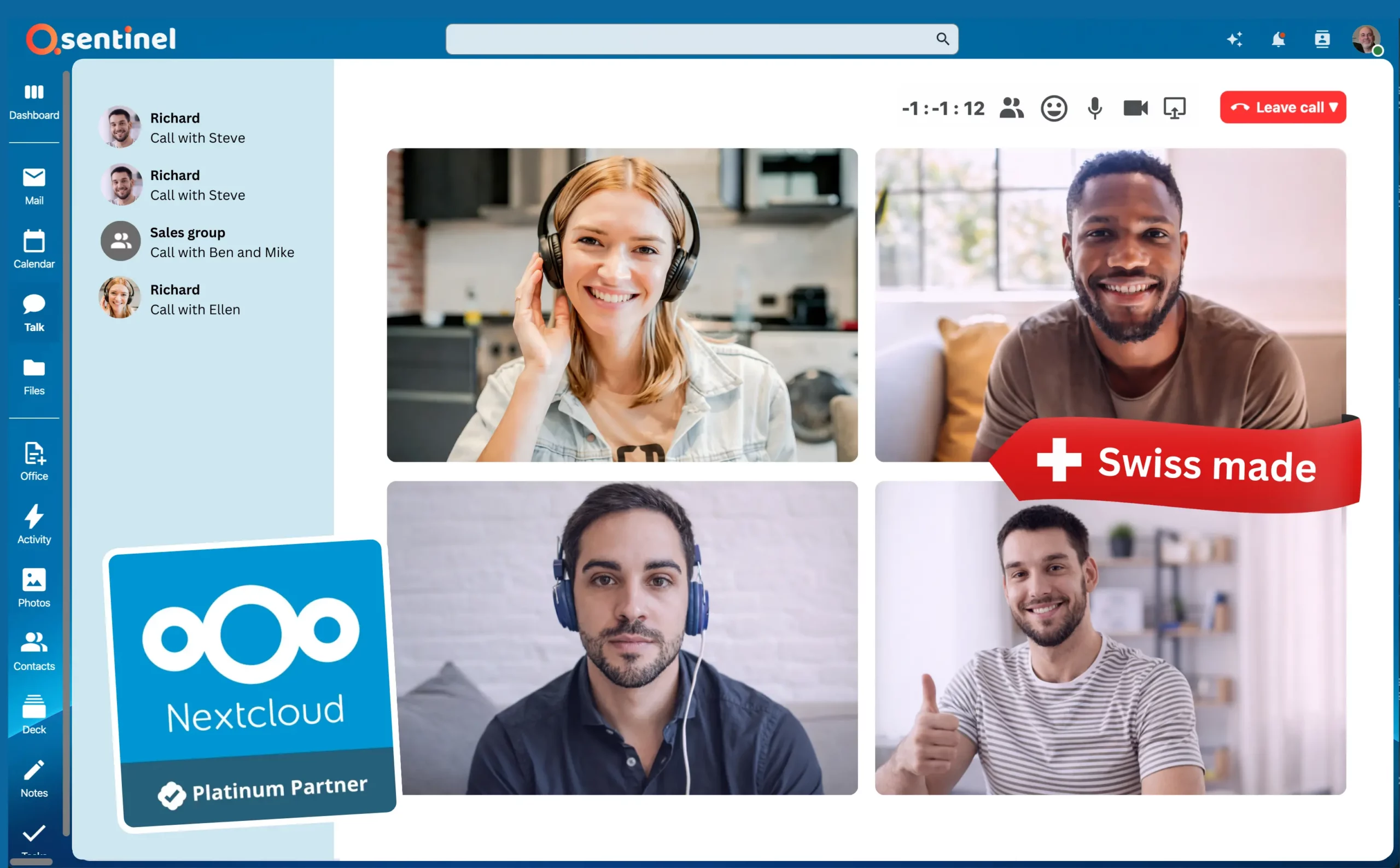
Powered by Nextcloud. Trusted by Millions of Users.
Why teams love working with Qsentinel
Familiar tools, smooth workflows, all without Big Tech exposure

Powered by Nextcloud. Trusted by Millions of Users.
Why teams love working with Qsentinel
Familiar tools, smooth workflows, all without Big Tech exposure


Zero Compromise Cyber Protection
While you work you are protected by industry leading cyber security

Zero Compromise Cyber Protection
While you work you are protected by industry leading cyber security

“If you believe in user freedom, data privacy and decentralization, Qsentinel is what you should be looking at.”
Jon maddog Hall | Emeritus chair of the Linux Professional Institute

“If you believe in user freedom, data privacy and decentralization, Qsentinel is what you should be looking at.”
Jon maddog Hall | Emeritus chair of the Linux Professional Institute
No budget draining consultants or exploding timelines
Migrate from legacy providers with our patented file migration technology
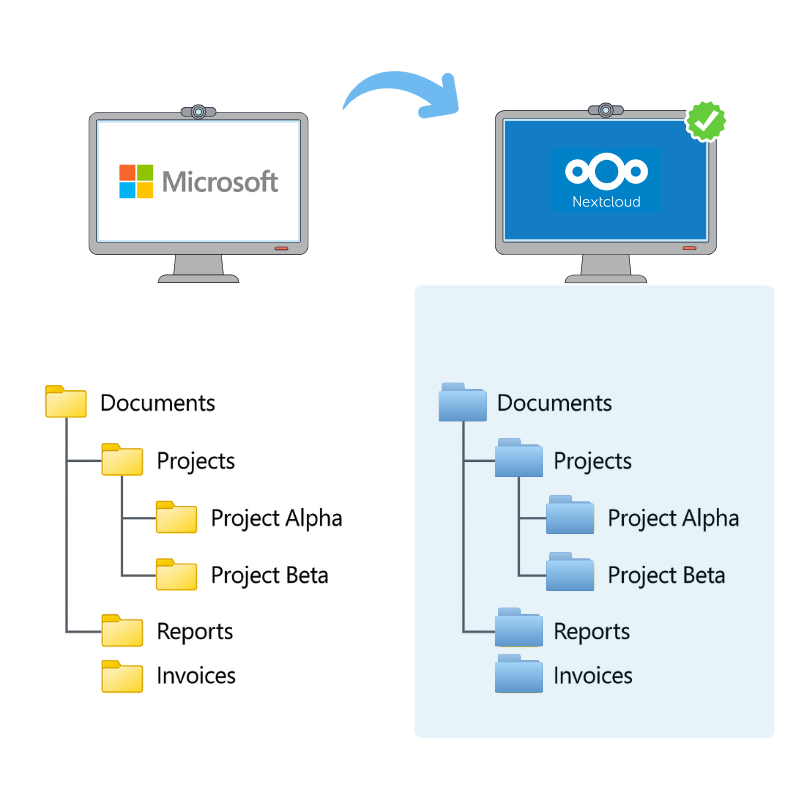
Data migration can be a challenge. Years of files that need to move without breaking anything. For most organizations, this is where timelines explode and costs spiral.
Qsentinel’s patented migration technology moves entire environments from Microsoft to Qsentinel, exactly as they are:
No budget draining consultants or exploding timelines
Migrate from legacy providers with our patented file migration technology
Data migration can be a challenge. Years of files that need to move without breaking anything. For most organizations, this is where timelines explode and costs spiral.
Qsentinel’s patented migration technology moves entire environments from Microsoft to Qsentinel, exactly as they are:

Built-in Access to our Private 10.000+ GPU AI Cluster
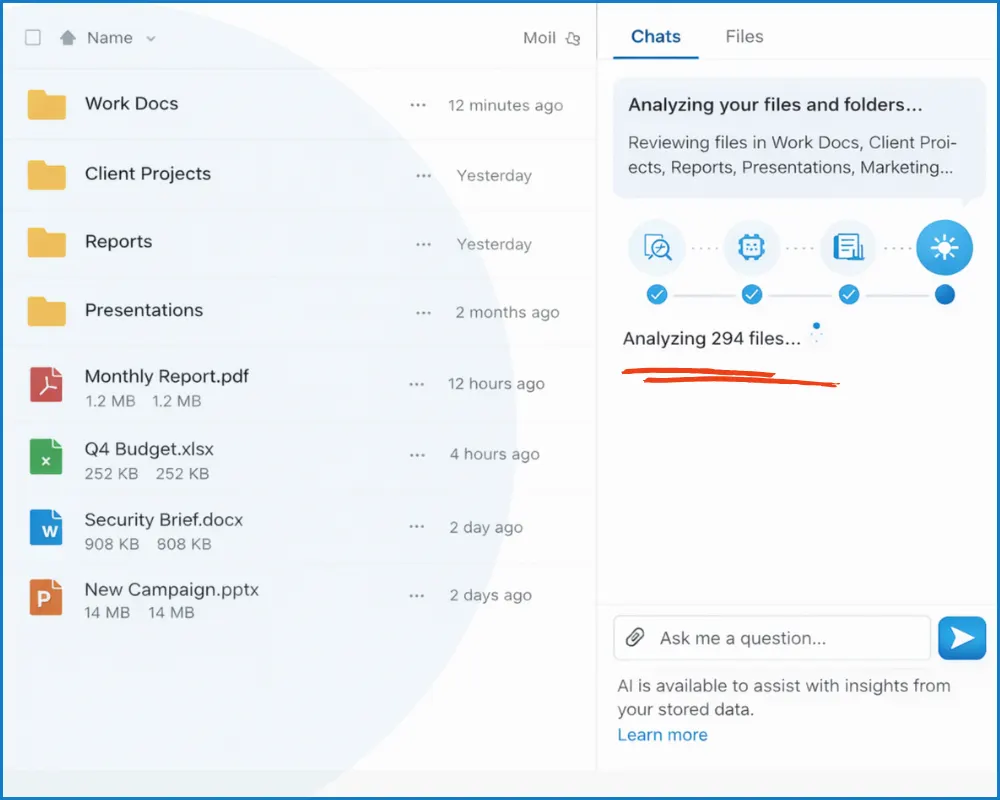
Integrated powerful Private AI. Analyze thousands of sensitive files at once.
Public AI platforms impose strict upload limits, break your workflow, and quietly feed your data back into their training pipelines.
With Qsentinel private AI, you work without limits, analyze thousands of files at once, providing unprecedented insights.

Built-in Access to our Private 10.000+ GPU AI Cluster
Integrated powerful Private AI. Analyze thousands of sensitive files at once.
Public AI platforms impose strict upload limits, break your workflow, and quietly feed your data back into their training pipelines.
With Qsentinel private AI, you work without limits, analyze thousands of files at once, providing unprecedented insights.
Need more answers?
Latest news
Stay informed with articles on data sovereignty, post quantum security, compliance, NIS-2 and more.
Knowledge base
Become a reseller
Contact us to benefit from the exponentially growing cyber security market and data sovereignty landscape.
Read more